- Joined
- Jan 27, 2017
- Messages
- 1,008
- Likes
- 828
- Points
- 813
SQLi Dumper v.9.7
SQLi Dumper v.9.7 - database dump harvester. Finds and promotes sql and XSS vulnerabilities on vulnerable sites and outputs ready-made email databases; pass. You don't need to be a seven-spade or some kind of cool hacker to use this software. It's simple:
==========
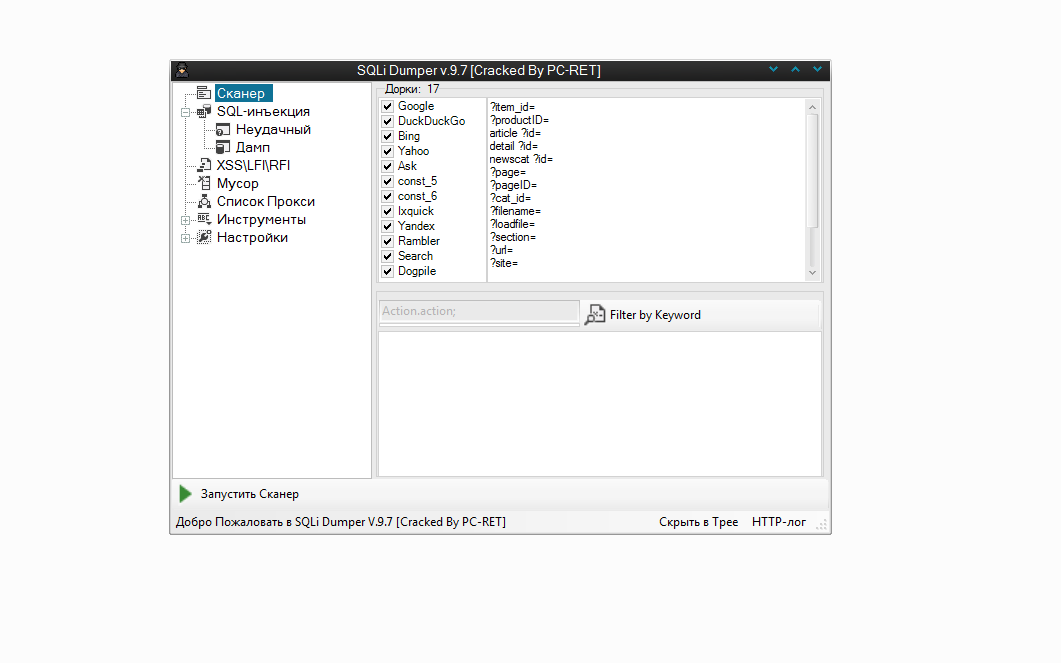
Before starting work, it is better to expand the program to full screen so that all the controls would fit. Find a list of live proxies on the network (you can parse without them, but it's better with them). Copy them to the clipboard, in SQLi Dumper go to the "Proxy List" tab and click on the "Apprend" button in the upper left corner, a small window will appear where you need to select the type of your proxies and click "ok", the proxies will be loaded into the program. If you wish, you can check them for validity right in the program, for this we press the "Check Proxy" button in the upper right corner. After the proxies are checked, right-click on them -> Select All and click the checkbox next to any of them, so we will select all the proxies for work. That's all with the proxies.
The second thing we need is dorks. There are a lot of them and it is easy to google them on the Internet, there are already several in SQLi Dumper v.9.7 . Right in the window with the dorks, you can / need to add some keywords through the space in order to diversify the search, for example:
That's all! We press "Launch Scanner" and wait for the end of the process.
After the links are parsed, go to the "SQL Injection" tab and click "Run Exploiter" at the bottom left, waiting for the end.
In a good scenario, in this tab you will have several sql vulnerable links, and we will work with them.
Click on any link pr. Book. mouse -> Dump, you will be transferred to the "Dump" tab.
Select any database you like and click "Get Tables", among the tables we need to find something like "admin" or "users", select it and click "Get Columns", but in the columns that appear we are looking for "email" and " password "(variations may be different), put a checkmark in front of them and click" Data Dump ":
Thus, databases are extracted using sql injections.
In ancient versions of engines, passwords are in cleartext. But basically, passwords are encrypted using the md5 or md5 method (md5 ($ pass)), they are decrypted by brute force using the wonderful PasswordsPro program .
Password 1111
DOWNLOAD
Password 1111
Last edited:








